Setup is easy
- Register on https://store.opendns.com/get/home-free
- Update your home router configuration with DNS server provided
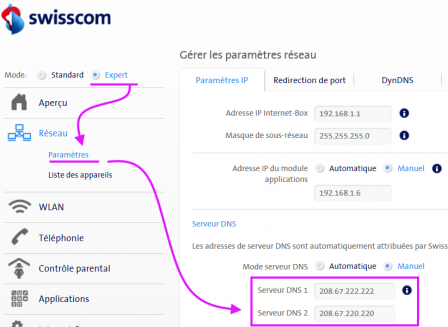
Swisscom router configuration
If you are interested to get some stats back, you have to inform OpenDNS with your static IP. As I don't pay for that, my provider is dynamically changing it. You will then need to setup a DNS updater client (for Windows, for MacOS).
But I have a Raspberry Pi at home (running Raspbian) dedicated for some experiments and I decided to use it for that pupose. I have to say that I thought to my Synology NAS but finally prefer not to touch it with some configuration changes.
EDIT: I discussed this at work and it should exists a Synology feature that could be used to update your IP on OpenDNS.
Update package cache and install a Dynamic DNS updater:
$ sudo apt-get update && apt-get install ddclient
The setup wizard will certainly ask you some parameters. You will be able to fill that in using the extract on my ddclient.conf:
# /etc/ddclient.conf # Update every 10 minutes daemon=600 protocol=dyndns2 use=web, web=http://myip.dnsomatic.com server=updates.opendns.com login=YOUR E-MAIL ADDRESS USE TO REGISTER TO OPENDNS.COM password=YOUR PASSWORD FOR OPENDNS.COM NAME OF MY PERSONAL NETWORK (NAMED ON OPENDNS.COM)
You can also re-generate the configuration file, using the wizard:
$ sudo dpkg-reconfigure ddclient
Then, verify/update the configuration:
$ sudo nano /etc/ddclient.conf
And test your configuration
$ sudo ddclient -query
(re-) Start the service and check the log
$ sudo service ddclient restart $ tail /var/log/syslog
You should see a successful update, depending on the lease duration.
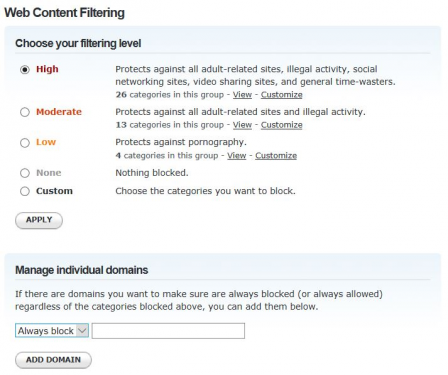
Settings on OpenDNS.com
Under the settings, on OpenDNS.com, you will be able to select the level of security, block certain website categories and configure your custom webpage in case of block. A blacklist/whitelist is also possible.
If you want to go with this, I assume you will have to spend your time into tuning it (and building the whitelist). For instance, blocking the webmail will result in blocking all Office365 trafic (mail, onedrive, onenote, etc) :-/ .
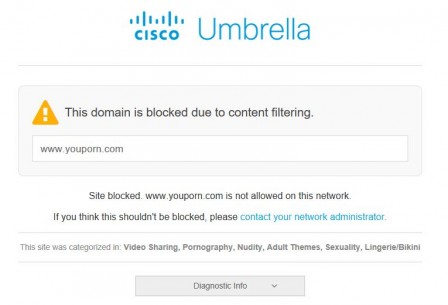
Message to user
And when you test the access, you should get this kind of webpage:
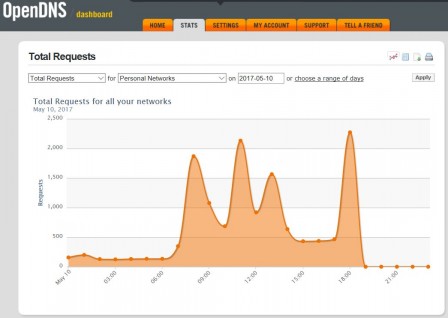
Statistics and reporting
Some stats and reporting are also provided. That's really where you understand they know a lot about you, your habits and the web sites your are surfing on. You can disable this part, if not needed. But it could be interesting to see if some domains are blocked (for security reasons) or what kind of domains you are requesting a lot. I discovered that my Samsung TV generates some 'unwanted' trafic, as well as my Philips HUE bridge....
And if my provider is IPv6 enabled (dualstack)?
Swisscom provides me with IPv6 connectivity (6rd) and OpenDNS supports IPv6, as stated in a community post.
However, I couldn't fully test the service, because my router only allows IPv4 for DNS resolution.
I plan to use my Raspberry to test this very soon.